Plantronics headsets on Windows
De ceva timp am un headset Plantronics pe care il folosesc impreuna cu telefonul mobil. La un moment dat am vrut sa il folosec si cu aplicatiile de pe laptop insa nu am reusit datorita lipsei driverelor.
Dupa ceva investigatii am descoperit ca instalarea este totusi posibila si pe Windows folosind driverele de la Broadcom:
https://www.broadcom.com/support/bluetooth
vCenter Server 6.0 – Skip Install Prerequisites
VCenter Server 6.0 are niste cerinte hardware destul de mari asa ca daca incerci sa il instalezi pentru un simplu laborator si ai anumite limite hardware o sa ai o problema. Sa aloci 8Gb de RAM doar ca sa instalezi vCenterul mi se pare o monstruozitate.
Totusi, undeva ascuns se afla un parametru care face ca installerul sa treaca mai departe chiar daca nu sunt indeplinite cerintele hardware.
Parametrul se numeste SKIP_HARDWARE_CHECKS si va trebui sa lansati setup-ul din linie de comanda in felul urmator:
VMware-vCenter-Server.exe “SKIP_HARDWARE_CHECKS=1”
MS16-071 – Patch Now
A trecut o saptamana de cand a fost publicat security bulletinul pe luna Iunie si vad ca lumea nu se grabeste instaleze nimic.
Dar MS16-071 e motivul pentru care trebuie sa urgentati update-ul pe server. Este remote exploitable, foloseste un protocol ce este foarte usor permis prin firewall-uri, iar serviciul afectat ruleaza in multe cazuri pe domain controllere. Deci exista toate sansele ca cineva sa te faca sah mat fara ca tu sa apuci sa iti dai seama.
Sapatamana trecuta nu exista nici un semn ca ar exista un exploit code deja functional. Dar cum vulnerabilitatea a fost expusa in privat direct catre Microsoft, probabil ca o sa mai dureze ceva timp pana o sa existe ceva pentru publicul larg. Dar asta nu inseamna ca nu exista parti ce stiu cum sa exploateze aceasta vulnerabilitate.
Windows DNS Server Use After Free Vulnerability – CVE-2016-3227
A remote code execution vulnerability exists in Windows Domain Name System (DNS) servers when they fail to properly handle requests. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. Windows servers that are configured as DNS servers are at risk from this vulnerability.
To exploit the vulnerability, an unauthenticated attacker could send malicious requests to a Windows DNS server. The update addresses the vulnerability by modifying how Windows DNS servers handle requests.
Microsoft Security Intelligence Report
Nu m-am mai uitat pe SIR de foarte mult timp, dar ultimele editii sunt super interesante si trebuie sa imi fac timp sa le citesc.
https://www.microsoft.com/security/sir/default.aspx
Privileged Access Management in Windows 2016 Active Directory
So this PAM (Privileged Access Management) stuff is something I thought I need to write it in English since there is not so much information about it. This feature is something that Microsoft is making a big fuss on how to use it with MIM (Microsoft Identity Manager) but not on how to leverage at least part of it if you don’t have MIM.
Some info on this new technology is here:
https://technet.microsoft.com/en-us/library/dn903243.aspx
And from this link let’s look a little bit at the problems PAM is trying to solve:
A real concern for enterprises today is the uncertainty regarding resource access within an Active Directory environment. Particularly troubling is news about vulnerabilities, unauthorized privilege escalations, and other types of unauthorized access, including pass-the-hash, pass-the-ticket, spear phishing, and Kerberos compromises. All of these attack capabilities are a concern for enterprises.
Could their Active Directory environment already be compromised? If not, how long can it take an attacker to find and then compromise a Domain Admins account? After attackers achieve such access, what can stop them? How long can they lurk on the network with that access? How long can the environment be at risk before the compromise is detected? Attackers can leave backdoors (create a way that allows them to get back in but not using the normal procedures), perform data exfiltration, and carry out other exploits.
The goal of PAM is to change the timeframes in which these vulnerabilities can be exploited. Today, it’s too easy for attackers to obtain Domain Admins account credentials, and it’s too hard to discover these attacks after the fact. Along with other investments, PAM will make it harder for attackers to penetrate a network and obtain privileged account access. PAM adds protection to privileged groups that control access across a range of domain-joined computers and applications on those computers. It also adds more monitoring, more visibility, and more fine-grained controls so that organizations can see who their privileged administrators are, and what are they doing. PAM gives organizations more insight into how such administrative accounts are used in the environment.
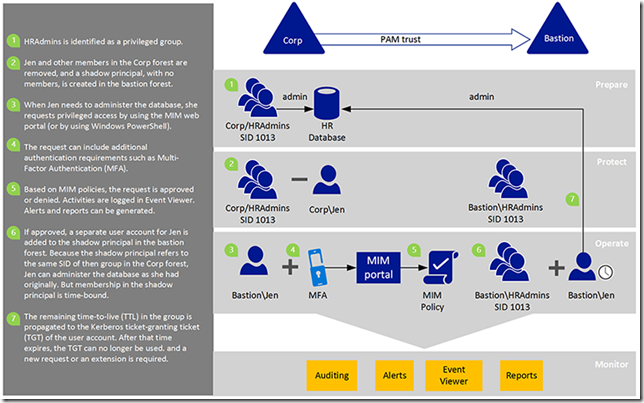
So … here’s a quick look on how this new PAM is going to work:
– a new Active Directory forest will be created
– all privileged accounts will be created in the new forest (let’s call it a bastion Active Directory forest)
– the old production forest doesn’t require any upgrade (for now)
– a new type of trust will be created between these two forests (PIM Trust)
– shadow groups (a new type of objects available in WS 2016) will be created in the bastion forests
– each time an admin will need to execute his/her work, the account in the bastion forest will be used (and that account will have access in the production forest, without being a member of any privileged groups)
The following picture will give some more insight of the workflow:
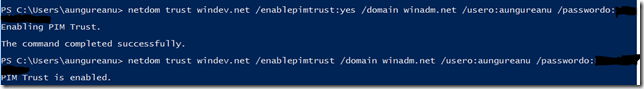
And let’s get started. We have the new bastion forest. We have the trust set between these two forests and we’ll need to enable one more thing over this trust. Using NETDOM with the /ENABLEPIMTRUST option:
Note:My production forest is called WINDEV.NET and my bastion forest is called WINADM.NET (sorry if this is confusing, but initially I had these set for another purpose).
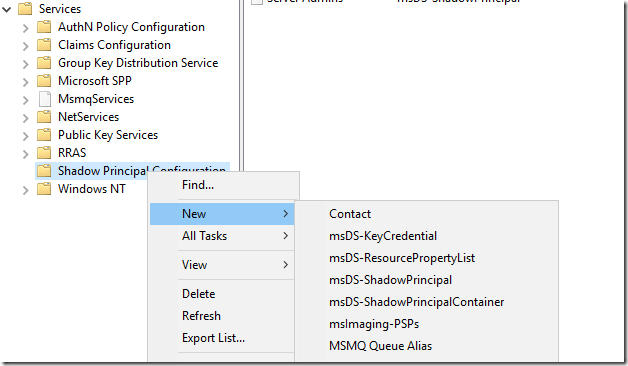
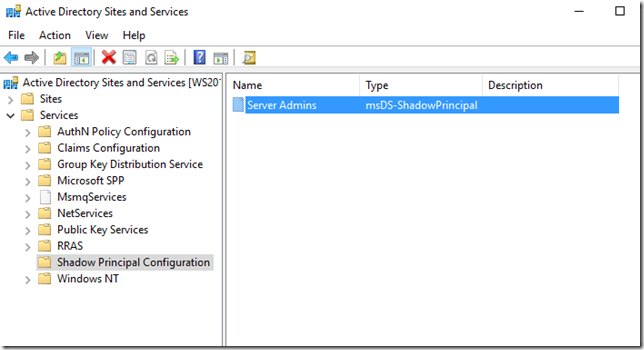
In the bastion forest, if we look in Active Directory Sites and Services console, we can see a new container called Shadow Principal Configuration and if we right click on it we have the option to create some new objects.
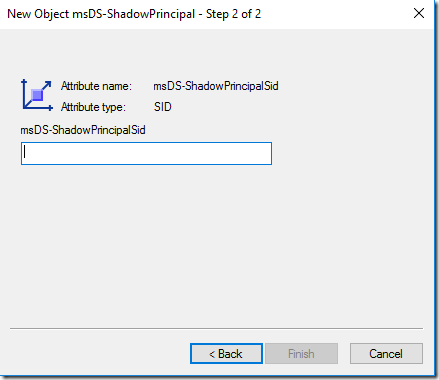
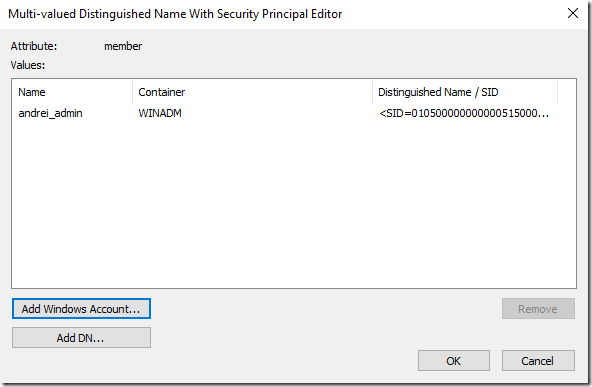
What we are interested in is the msDS-ShadowPrincipal (we can create these type of objects in some other parts of AD using Active Directory Users and Computers but for the scenario I am trying to show right now it doesn’t seem to produce the desired results; so let’s create this using Sites and Services).
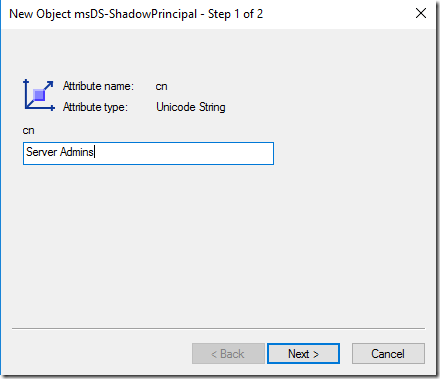
The new object will need a name. The object will be a shadow of an existing object from the production forest. And I am trying to shadow the Server Admins group.
Find out the SID of the production group (get-adgroup should be simple enough – in the production forest).
Just two steps and we have the shadow created.
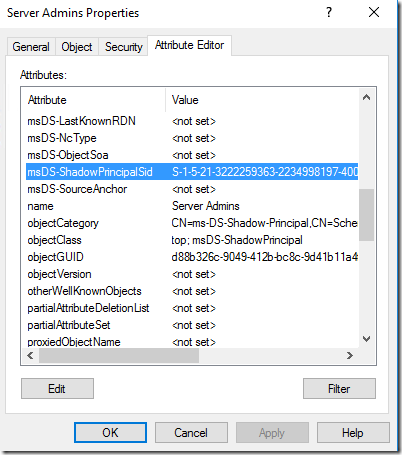
Let’s inspect the attributes of the new object:
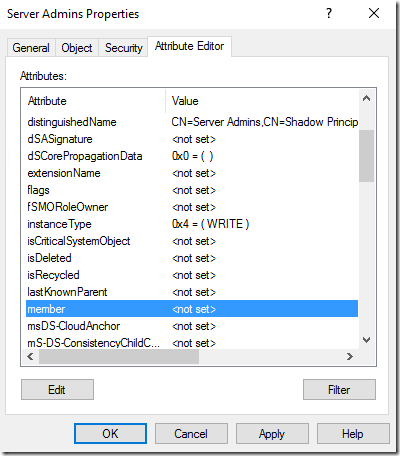
Now let’s add members to this shadow group. The members need to be accounts from the same forest as the shadow group (the bastion forest). So, my admins we’ll get new accounts that we’ll be regular accounts in the bastion forest, but through the shadow group they’ll be able to get privileges in the production forest.
And I have such an account that I will use for this:
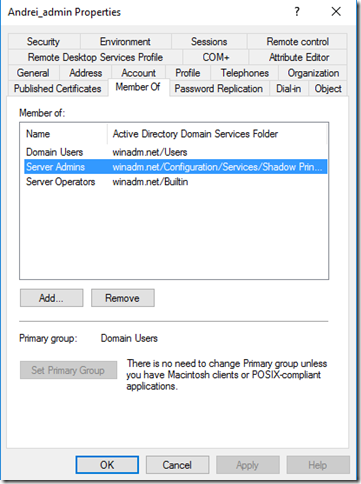
After this, the shadow group membership can be seen through the regular Active Directory Users and Computers console:
And now the test. I am logging on using the my “admin” account created in the bastion forest (WINADM), on a computer from the production forest (WINDEV).
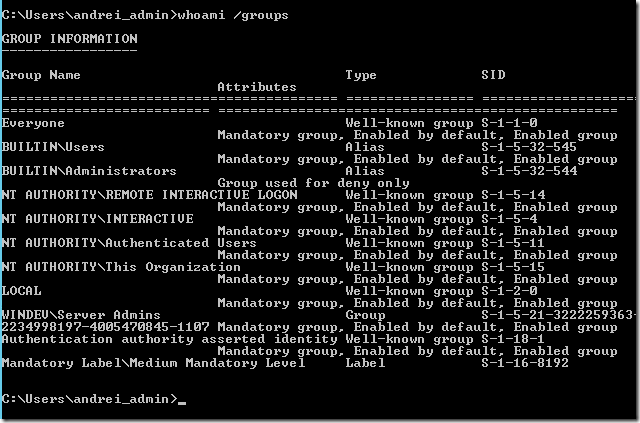
Running whoami /groups will show me that in my token, I have the SID of my Server Admins group from the production forest (WINDEV).
Combine these with time limited group membership and you will make a big change in your Active Directory security. Please note that for now this is beta software. Do not use it in production environments.
For now I am still waiting for the official product documentation …
Windows Server 2016 TP5
Tocmai ce s-a lansat WS2016 TP5, probabil ultimul technical preview inainte de RTM. Poate fi downloadat de aici:
https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-technical-preview
Documentatia e cam subtire in acest moment. Tot ce am putut gasi este in link-ul de mai jos:
https://technet.microsoft.com/en-us/library/dn765472(v=ws.12).aspx
Delprof2 – User Profile Deletion Tool
Pe vremuri exista un tool oferit de Microsoft numit Delfprof ce ajuta in stergerea profilelor inactive. Din pacate tool-ul nu mai poate fi folosit pe sistemele de operare mai noi.
In schimb exista un tool third party numit Delprof2 oferit de HedgeKlein ce ruleaza pana la Windows 8 (inca nu am avazut nimic legat de Windows 10).
https://helgeklein.com/free-tools/delprof2-user-profile-deletion-tool/
Tool-ul e util si atunci cand ACL-urile impiedica accesarea profilelor. Nu si atunci cand profilul e “in use”.
Poate fi folosit si remote si doar pentru a face o evaluare a profilelor de pe un anumit sistem.
NTDS.DIT Forensincs
M-am gandit sa partajez aici cateva materiale despre atacurile offline asupra bazei de date Active Directory, NTDS.DIT. Nu le vad ca pe hacking, ci mai mult educationale. Contin multe informatii nedocumentate ce va ajuta sa intelegeti cum functioneaza Active Directory si va deschid ochii asupra atacurilor existente.
http://ntdsxtract.com/downloads/ntdsxtract/ntds_forensics.pdf
http://www.dataforensics.org/microsoft-active-directory/
http://moyix.blogspot.ro/2008/02/syskey-and-sam.html
PS: acum cred ca e clar de ce accesul fizic la un DC cu discul necriptat este o grozavie.
Temporary Group Membership in Windows Server 2016
Microsoft nu a uitat complet de Active Directory si in versiunea ce vine cu Windows Server 2016 sunt cateva imbunatatiri subtile. Oricum am fost obisnuiti ca pe partea de AD, schimbarile sa fie foarte subtile si greu de observat pentru adminul neexperimentat.
Una din noutati se numeste Temporary Group Membership si vine cumva mai mult pentru a face Privileged Access Management prin Microsoft Identity Manager insa poate fi folosita si standalone, fara MIM.
Dar sa revenim strict la subiect, Temporary Group Membership face exact ce spune si numele. Adauga membri intr-un grup, pe o perioada determinata. Exemplu: cineva iti cere access intr-un grup pentru a efectua anumite taskuri, sa zicem Domain Admins, cererea ii este aprobata si ai permisiunea sa ii dai acces dar doar pentru 3 zile. Cu aceasta optiune in place poti adauga userul in grup si seta un Time to Live de 3 zile. Cand timpul va expira, userul va fi scos din grup automat fara a fi nevoie de interventia administratorului.
Noile functionalitati ce vin cu versiunea 2016 se activeaza separat si odata activate nu se mai poate face rollback. Cam la fel cum a fost si pana acum (gen AD Recycle Bin).
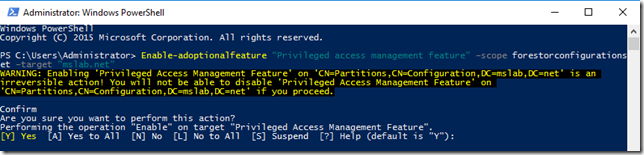
Activarea se face folosind comanda powershell Enable-ADOptionalFeature.
Enable-adoptionalfeature “Privileged access management feature” –scope forestorconfigurationset –target "mslab.net".
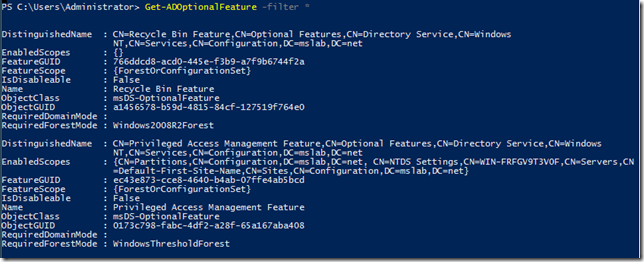
Daca dorim sa verificam prezenta functionalitatii intr-un forest existent putem folosi Get-AdOptionalFeature:
Odata activata functionalitatea, folosim optiunea –MemberTimeToLive a comenzii Add-ADGroupMember. Comanda va seta un TTL pe link-ul ce defineste membrul in grup. Prima data va trebui sa definim acel TTL folosind New-TimeSpan:
$ttl = New-TimeSpan -Minutes 5
Add-ADGroupMember -Identity "Domain Admins" -Members aungureanu -MemberTimeToLive $ttl
Iar din aces moment, userul nou adaugat are fix timpul definit ca memberTimeToLive pentru a isi efectua taskurile. In momentul in care timpul a expirat, userul este automat scos din grup si mai mult decat atat, tichetul Kerberos va fi si el expirat (in momentul emiterii tichetului de catre KDC acesta va seta lifetime-ul ca fiind TTL-ul cel mai mic de pe link-urile ce au aceasta optiune activata; iar fiecare DC va verifica tabela cu link-urile ce urmeaza sa expire si le va sterge atunci cand TTL-ul va ajunge la zero)
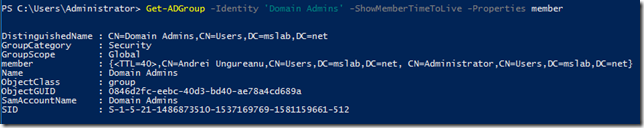
Putem sa verificam apartenenta la grup si timpul ramas folosind Get-ADGroup:
Dupa cum vedeti forward link-ul din grup are acum un nou format cu <TTL=40> in fata DN-ului. TTL-ul de acolo reprezinta timpul ramas in secunde, in cazul nostru 40.
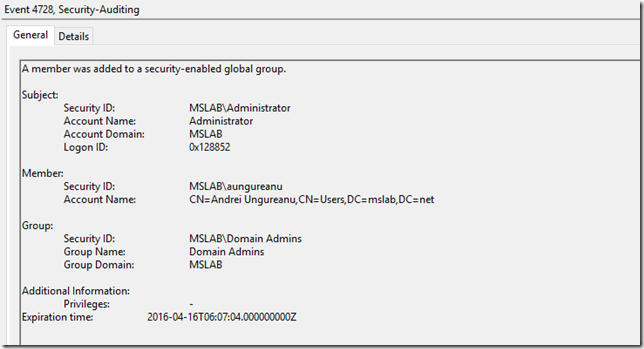
In event viewer se va putea vedea in afara de momentul in care a fost adaugat userul in grup si “Expiration time”:
Deocamdata nu a gasit nici un eveniment prin care sa monitorizez ca userul a fost scos din grup.
Dar considerand ca ca produsul este inca beta, mai sunt de asteptat schimbari legate de aceste noi functionalitati.
Encrypting credentials with Powershell
Rasfoind cateva site-uri am citit despre cum poti sa stochezi criptat credentiale ce pot fi refolosite mai departe in scripturi. Metodele folosite sunt interesante si sunt utile in unele cazuri: